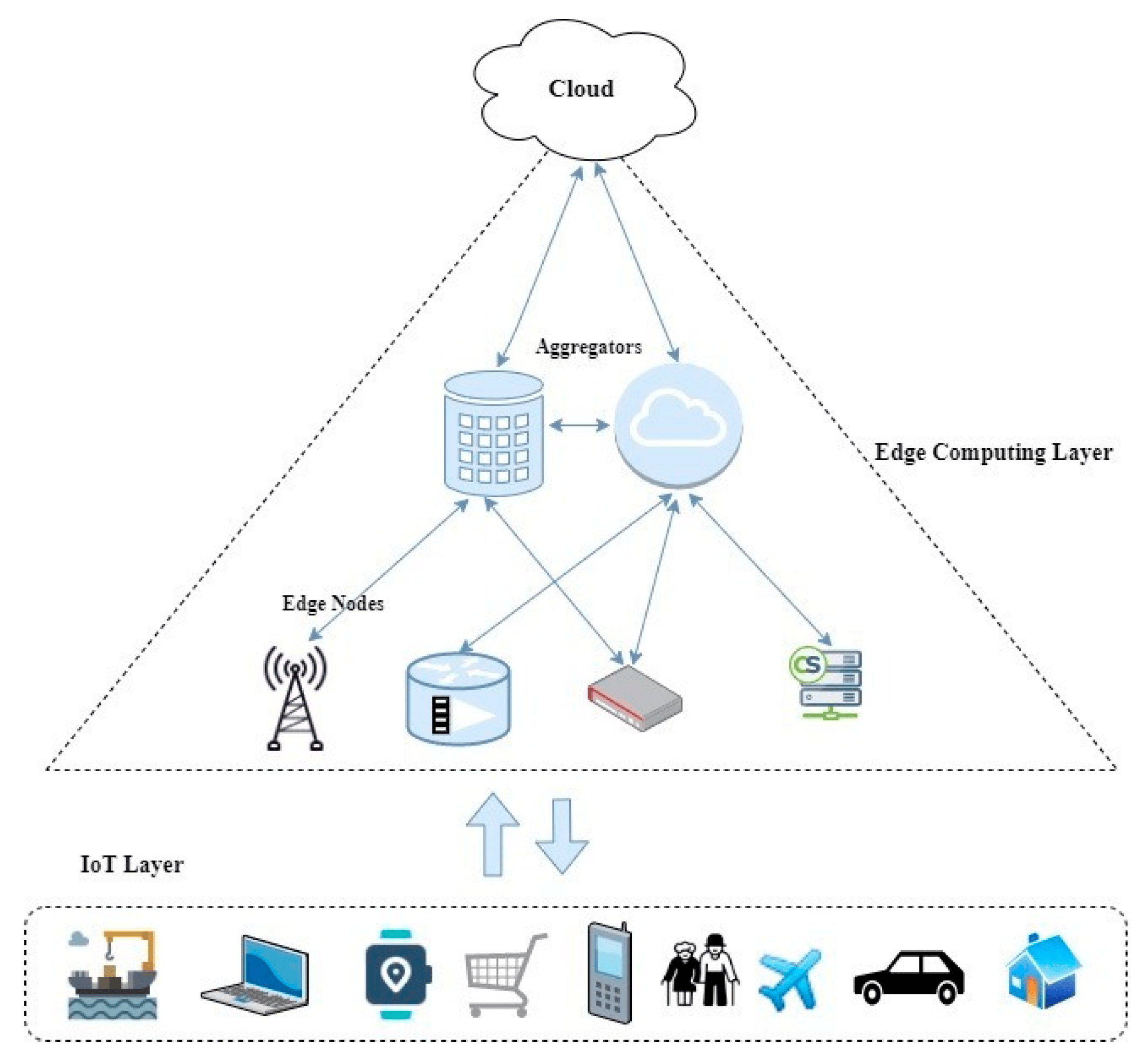
The Internet of Things (IoT) has revolutionized how we live and work. From smart home devices to industrial sensors, IoT devices bring unparalleled convenience and efficiency. However, beneath their innovative allure lies a growing concern: IoT devices can become gateways for cyber threats, compromising the very networks they’re designed to enhance.
In this article, we’ll uncover the hidden dangers posed by IoT devices and explore strategies to safeguard your network.
1. Why IoT Devices Are a Security Risk
IoT devices are built for functionality, often prioritizing usability over robust security. This makes them vulnerable to attacks, such as:
- Weak Authentication: Many devices come with default usernames and passwords that users forget to update.
- Unpatched Firmware: Manufacturers may not provide regular updates, leaving devices exposed to vulnerabilities.
- Limited Resources: Low-power IoT devices lack advanced encryption and security features.
- Network Overexposure: IoT devices are often connected directly to the internet, increasing their attack surface.
2. Common Threats from IoT Devices
a. Botnets and Distributed Denial of Service (DDoS) Attacks
Hackers can exploit poorly secured IoT devices to form botnets, launching large-scale DDoS attacks on targeted servers or networks.
b. Data Breaches
IoT devices collect vast amounts of data. If hacked, sensitive information such as user habits or business processes can be exposed.
c. Unauthorized Network Access
A compromised IoT device can act as a backdoor, allowing attackers to infiltrate your network and gain access to critical systems.
d. Malware Propagation
IoT devices can spread malware across connected devices, infecting an entire network.
3. How IoT Threats Can Impact Businesses
For SMBs, the consequences of compromised IoT devices can be devastating:
- Operational Disruptions: Attacks can halt critical business processes, affecting productivity and revenue.
- Financial Losses: Recovering from breaches and downtime can result in significant costs.
- Reputational Damage: Data breaches erode trust, impacting customer relationships and brand image.
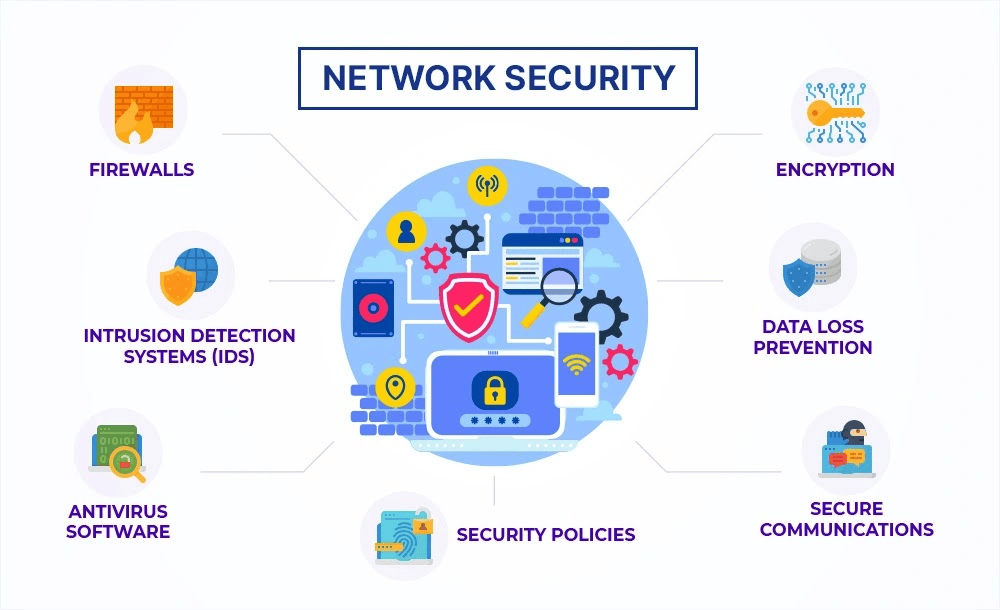
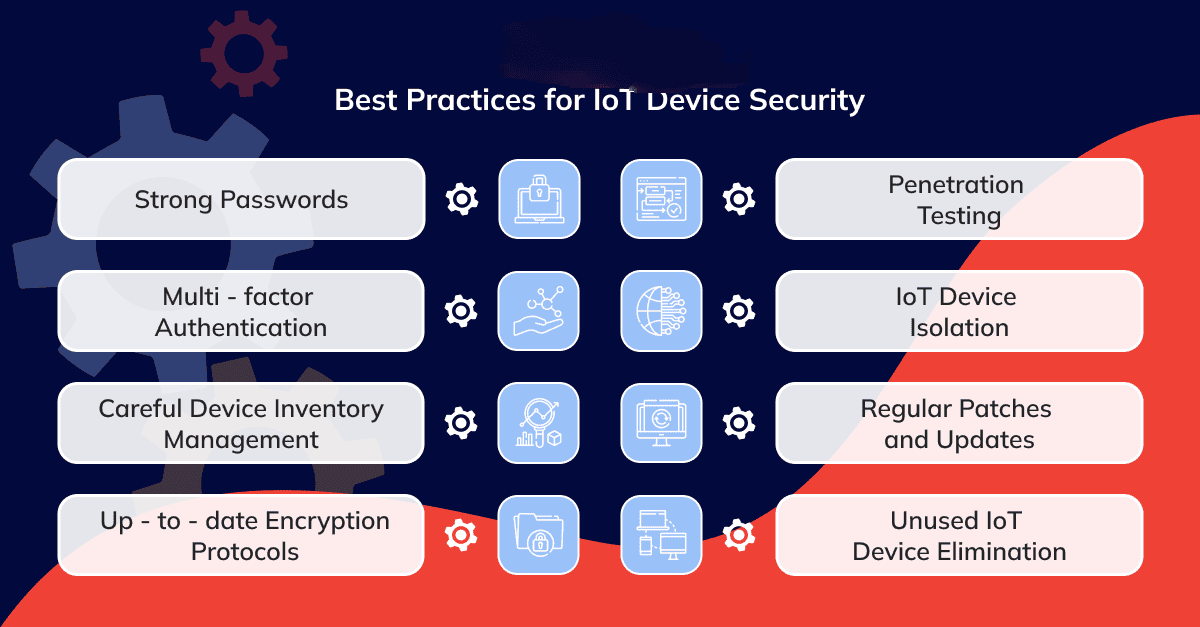
4. Strategies to Secure IoT Devices
a. Change Default Credentials
Always update default usernames and passwords during setup. Use strong, unique passwords for each device.
b. Update Firmware Regularly
Ensure all IoT devices have the latest firmware installed to address known vulnerabilities.
c. Isolate IoT Networks
Segment IoT devices on a separate network to minimize the risk of lateral movement if a device is compromised.
d. Enable Encryption
Use encryption protocols for data transmission between IoT devices and servers.
e. Monitor Network Traffic
Employ tools to monitor unusual traffic patterns that could indicate a breach
5. Choosing Secure IoT Devices
When purchasing IoT devices, consider:
- Manufacturer Reputation: Opt for devices from companies with a proven commitment to security.
- Update Policies: Check whether the manufacturer provides regular updates and patches.
- Built-in Security Features: Look for devices with robust authentication and encryption options.
6. The Role of IoT in a Secure Network Environment
IoT devices can enhance your operations without compromising security if integrated responsibly. Develop a comprehensive IoT security policy that includes:
- Regular audits of connected devices.
- Employee training on IoT risks and best practices.
- Collaboration with IT partners for advanced monitoring and threat detection solutions.
Conclusion: Balance Innovation with Security
IoT devices offer incredible potential but must be deployed with care. By understanding the risks and implementing proactive measures, you can enjoy the benefits of IoT without jeopardizing your network security.
Don’t let hidden threats undermine your operations—take steps today to secure your connected future.










Leave a comment